Zero Trust Implementation Guide
Methodology deployment verify iterative ease palo networks suggests alto A holistic approach to creating a zero-trust enterprise What is zero trust security? principles of the zero trust model (2022)
Unveiling the Future of Cybersecurity: Microsoft’s Zero Trust
A practical guide to a zero trust implementation Zero trust – the road towards more effective security – quicklaunch Beginner adopting
Trust zero microsoft model security implementing phase performed components major each figure work implementation diagram access services identity user
What is zero trust? by wentz wu, issap, issep, issmp cissp, ccsp, csslpSecurity adaptive visibility a10networks Zero trust security explainedImplementing a zero trust security model at microsoft.
Build a zero trust roadmapEmbracing a zero trust security model Unveiling the future of cybersecurity: microsoft’s zero trustMicrosoft zero trust security.
.jpg)
A practical guide to zero-trust security
Zero trust security modelThe zero-trust architecture imperative for financial services Zero trust architecture understanding the nist framework of zero trustWhy zero trust implementations remains a major challenge.
Understanding zero trust in 2023 (part-1)Practical 7wdata Zero trust implementationA beginner's guide to zero trust.

What is zero trust? zero trust security model
Zero trust model, architecture & implementationZero trust security model A practical guide to a zero trust implementation – atiForrester research: a practical guide to a zero trust implementation.
What is the zero trust model?Starter guide: what is zero trust architecture and where do you start? Unlock zero trust with 5 essential nist principlesWhat is zero trust and why is it so important?.

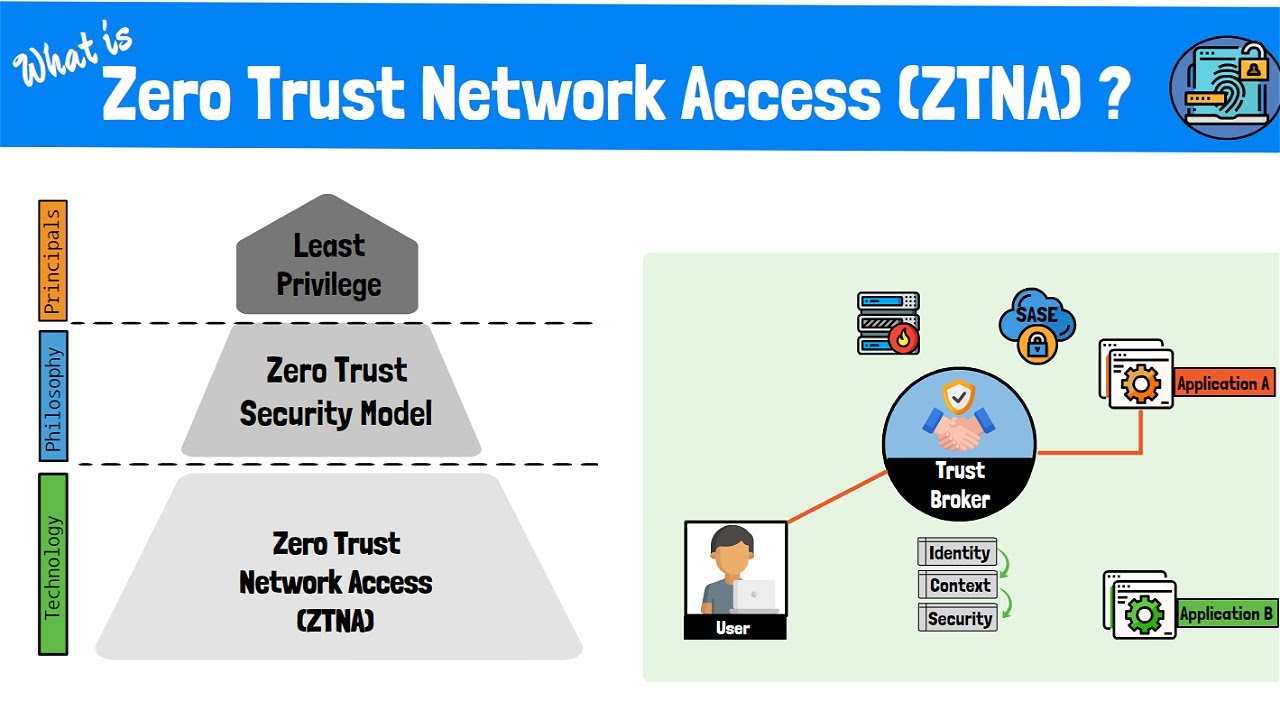
What is zero trust network access (ztna)? the zero trust model
Logrhythm maturity embracingZero trust là gì? tại sao nó lại quan trọng? Zero trust security: a modern approach to securing your applications🔒Wat is zero trust?.
Getting started with zero trust access management trust begins withPractical implementation jumpcloud Strategy to implementation with the zero trust advisory serviceZero trust model and its 7 principal elements outlined.